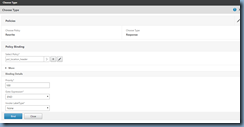
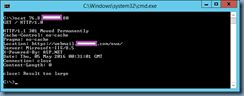
One of the most common Citrix NetScaler questions I’ve been asked by colleagues and clients is how to import a PFX certificate from a Microsoft Windows Server into Citrix NetScaler and while there is a KB from Citrix demonstrating this process via the GUI:
How to Convert PFX Certificate to PEM Format for Use with NetScaler
http://support.citrix.com/article/CTX136444
… there did not appear to be any instructions performing this via the command line so this post serves to demonstrate the process.
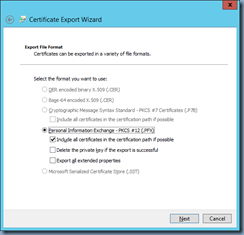
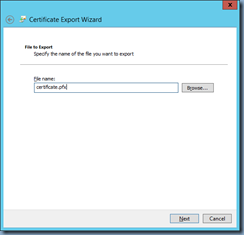
Step #1 - Export the certificate to PFX
Begin by logging onto the server with the certificate installed, launch the certificate store (certlm.msc) and export the certificate with the private key as a PFX:




Step #2 (Optional) - Export the certificate to CER
Exporting the certificate as a CER file without the private key is optional as you can create the CER file from the PFX file on the NetScaler but if you are performing the export from the Microsoft server, go ahead and create this file as well:


Note that you should export the file as Base-64:
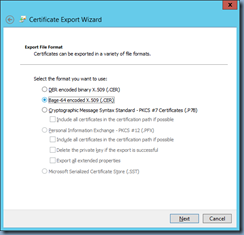

Step #3 - Upload PFX and CER file
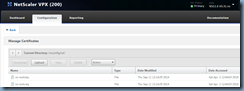
With the files exported, proceed to upload them to the NetScaler’s /nsconfig/ssl directory with either WinSCP or via the web management portal by navigating to Traffic Management > SSL then click on Manage Certificates / Keys / CSRs:

Use the Upload button to upload the files:
Step #4 (Optional) - CER file
If you’ve exported the certificate without the private key as a .cer file then this step could be skipped but if you had no control over the export and was only given a .pfx file then you can execute the following commands to generate the .cer file on the NetScaler:
shell
cd /nsconfig/ssl
openssl pkcs12 -nokeys -in certificate.pfx -out certificate.cer

You should now see a .cer file:

Step #5 - Generate .KEY file
The next file we will need to generate is the key file (also known as pem) using the uploaded PFX that contains the private key. Proceed by executing the following commands:
shell
cd /nsconfig/ssl
openssl pkcs12 -nocerts -nodes -in certificate.pfx -out tempcertificate.key -des3
openssl rsa -in tempcertificate.key -out certificate.key
rm tempcertificate.key

--------------------------------------------------------------------------------------------------------------------------------------------------------------------
***Note that the reason why we needed to create a tempcertificate.key file is because the following error would be thrown if we do not use the openssl rsa command to remove any hidden space control characters:
ERROR: Invalid private key, or PEM pass phrase required for this private key

See the following Citrix Knowledge Base article for more information:
ERROR: "Invalid private key, or PEM pass phrase required for this private key" on NetScaler Appliance
http://support.citrix.com/article/CTX134233
--------------------------------------------------------------------------------------------------------------------------------------------------------------------
The commands displayed above is the equivalent of the operations performed in the GUI demonstrated in the following screenshots:

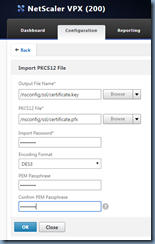
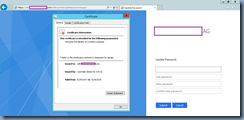
Step #6 – Installing Certificate onto the NetScaler
With the .key and .cer file on the NetScaler we can now proceed to install the certificate by executing the following command:
add ssl certKey www-contoso-com -cert certificate.cer -key certificate.key -password P@ssw0rd -expiryMonitor ENABLED -notificationPeriod 30
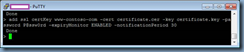
You can view the property details of newly installed certificate by executing the following command:
show ssl certKey www-contoso-com
The commands displayed above is the equivalent of the operations performed in the GUI demonstrated in the following screenshots:


![clip_image002[5] clip_image002[5]](https://lh3.googleusercontent.com/-C4xXz-V_e9o/VzyrPE2z7YI/AAAAAAAB8_Q/xCPtjOGF8q8/clip_image002%25255B5%25255D_thumb%25255B2%25255D.jpg?imgmax=800)
![clip_image002[7] clip_image002[7]](https://lh3.googleusercontent.com/-HKdy-sL3740/VzyrRiTndwI/AAAAAAAB8_Y/d7p6QoHgVXY/clip_image002%25255B7%25255D_thumb%25255B1%25255D.jpg?imgmax=800)





![clip_image002[6] clip_image002[6]](https://lh3.googleusercontent.com/-7rIUys4RG4Q/VzTglCi0xTI/AAAAAAAB88k/n-eOjWCpRsM/clip_image002%25255B6%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[8] clip_image002[8]](https://lh3.googleusercontent.com/-PYx83PlCKm4/VzTgnfy4nOI/AAAAAAAB88s/z7Z3M-tbD6U/clip_image002%25255B8%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[10] clip_image002[10]](https://lh3.googleusercontent.com/-at6Jrx4LAjo/VzTgpivTHTI/AAAAAAAB880/9kdiwAh9iG0/clip_image002%25255B10%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[12] clip_image002[12]](https://lh3.googleusercontent.com/-MtWy1_NwOno/VzTgsfYDNLI/AAAAAAAB888/0qAInI5-f6s/clip_image002%25255B12%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[14] clip_image002[14]](https://lh3.googleusercontent.com/-84cJfpNiNEg/VzTgu2lOIRI/AAAAAAAB89E/pGf3hTDc9uE/clip_image002%25255B14%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[16] clip_image002[16]](https://lh3.googleusercontent.com/-Td4XgY7NMVE/VzTgx3LKRhI/AAAAAAAB89M/3NZU-N8ca38/clip_image002%25255B16%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[20] clip_image002[20]](https://lh3.googleusercontent.com/-Vc2AsWAjGNI/VzTg2K9YKXI/AAAAAAAB89c/RnAr2NW7nnk/clip_image002%25255B20%25255D_thumb%25255B1%25255D.jpg?imgmax=800)