Wednesday, December 23, 2015
VMware Horizon View Virtual Desktops Stuck in Customizing Status
Tuesday, December 22, 2015
Event ID 1310 warning constantly logged on Exchange 2013 server
Your environment consists of the following:
- A single Exchange 2013 server with both the Mailbox and Client Access roles installed
- The version is 15.0 (Build 1156.6) - CU11
- The operating system is Windows Server 2012 R2 with the latest patches installed as of December 18, 2015
- global.asax
- web.config.bak
Monday, December 21, 2015
Using PowerShell cmdlets to remove accounts in Azure Active Directory
Most of the accounts that they wanted removed had the User Name format as:
The directory also had accounts with the format:
... which they did not want removed.
This particular directory did not have many accounts which meant manually remove them via the GUI was possible but I thought this would be a good opportunity to demonstrate how to use PowerShell cmdlets to filter and remove the accounts in bulk.
Begin by the launching WAAD (Windows Azure Active Directory) console execute Connect-MsolService and log in with the global or subscription admin account for the Azure Directory.
Once logged in, the cmdlet we'll be using to retrieve the set of users to be deleted is:
Get-MsolUser
https://msdn.microsoft.com/en-us/library/azure/dn194133.aspx
Note that every environment will be different so the following example will need to be tweaked accordingly.
The accounts I wanted to delete in this particular Azure directory all had the
o365admin@domain.onmicrosoft.com
With the above 2 requirements in mind, the 2 filters I needed for the Get-MsolUser cmdlet would be:
where-object {$_.UserPrincipalName -like "*domain.onmicrosoft.com"}
where-object {$_.UserPrincipalName -notlike "o365admin*"}
Combining the two filters together will create the following cmdlet:
Get-MsolUser | where-object {$_.UserPrincipalName -like "*domain.onmicrosoft.com"} | where-object {$_.UserPrincipalName -notlike "o365admin*"}
As mentioned earlier, every directory is unique and even if your environment matched this example, it is important to execute this cmdlet and review the returned accounts to verify no mistakes were made:
One of the annoyances I come across when working with PowerShell is that outputs such as the above tend to get truncated because of the length of the records so if you experience this, simply include the following at the end of the cmdlet:
| Format-Table -Wrap -AutoSize
The cmdlet would look as such:
Get-MsolUser | where-object {$_.UserPrincipalName -like "*domain.onmicrosoft.com"} | where-object {$_.UserPrincipalName -notlike "o365admin*"} | Format-Table -Wrap -AutoSize
The output would look as such:
Note that if the output above fills the screen buffer, you can pipe it to a txt file to review with:
> C:\userAccounts.txt
Once you have verified that the accounts retrieved are the ones that can be safely deleted, proceed with appending the following cmdlet to the end:
Remove-MsolUser
https://msdn.microsoft.com/en-us/library/dn194132.aspx
You should now see the accounts removed in the Azure GUI once the cmdlet successfully completes:
Friday, December 18, 2015
Hiding Citrix XenDesktop 7.x applications from PNAgent published Apps and Desktops
You’ve successfully configured a zero client to connect to your XenDesktop 7.x infrastructure via the URL:
https://yourStoreFrontFQDN.com/Citrix/StoreName/PNAgent/config.xml
… but would like to hide all of the published applications because the zero client will only be used for desktop access.
Solution
One of the ways to hide Applications or Desktops is to use the PowerShell cmdlet Set-DSResourceFilterType on the StoreFront server.
Begin by setting the execution policy to remote signed then importing the necessary Citrix PowerShell modules with the following cmdlets:
Set-ExecutionPolicy RemoteSigned
$dsInstallProp = Get-ItemProperty -Path HKLM:\SOFTWARE\Citrix\DeliveryServicesManagement -Name InstallDir
$dsInstallDir = $dsInstallProp.InstallDir
& $dsInstallDir\..\Scripts\ImportModules.ps1
Next, determine the Site ID of the IIS site hosting the StoreFront website:
With the Site ID determined, execute the following cmdlet to list what is being displayed for the store:
Get-DSResourceFilterType -SiteId 1 -VirtualPath "/Citrix/
For example:
Get-DSResourceFilterType -SiteId 1 -VirtualPath "/Citrix/Desktop"
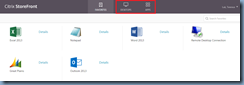
Notice the output above shows that Applications, Desktops and Documents are displayed meaning nothing is filtered out.
Next, execute the following cmdlet to filter out Applications and Documents thereby leaving only Desktops displayed:
Set-DSResourceFilterType -SiteId 1 -VirtualPath "/Citrix/Desktop" -IncludeTypes @("Desktops")
Executing the:
Get-DSResourceFilterType -SiteId 1 -VirtualPath "/Citrix/Desktop"
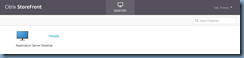
… will now show that only Desktops are included.
Logging into the zero client will now hide the applications that were displayed in the earlier screenshot:
Thursday, December 17, 2015
Attempting to connect to Citrix XenDesktop 7 from an HP t410 Smart Zero Client throws the error: “This client could not connect to a Citrix server at the address ‘https://yourStoreFrontFQDN.com/Citrix/StoreNameWeb”
You’ve configured a new HP t410 Smart Zero Client to connect to your Citrix XenDesktop 7.x StoreFront site but receive the following error message when you attempt to log in:
No Citrix Server
This client could not connect to a Citrix server at the address ‘https://yourStoreFrontFQDN.com/Citrix/StoreNameWeb
Solution
The reason why this error is thrown is because you have configured the connection’s Server URL with the Receiver for Web URL. To correct the issue, simply change the URL to:
https://yourStoreFrontFQDN.com/Citrix/StoreName/PNAgent/config.xml
You should be able to log in after the URL is changed:
Wednesday, December 16, 2015
Attempting to connect to a Citrix XenDesktop 7 store secured with internal CA throws the error: “CA certificate required to connect to this server is not installed or found…”
You’re in the process of configuring a new HP t410 Smart Zero Client with a XenDesktop 7.x infrastructure. You proceed to configure the zero client to connect to StoreFront 3.0.1 but quickly notice the following error message:
Certificate error
CA certificate required to connect to this server is not installed or found. Please use Certificate Manager to add the CA certificate or contact your system administrator.
Solution
The reason why this error is thrown is because the certificate presented by the StoreFront to secure the traffic between itself and the zero client is issued by an internal Microsoft CA which the zero client does not trust. To correct this issue, simply export the root certificate as Base-64 encoded X.509 (.CER) format:
Then navigate into the Certificate Manager of the zero client and import it into the Local Root Certification Authorities:
You should now be able to log into the site without receiving the certificate error message.
Windows 10 installation on a Dell Latitude E5550 loops back to the start of the installation screen
The reason why the installation loops back to the beginning is because legacy boot is turned on. To continue to the install, either manually select the UEFI Boot: Windows Boot Manager option:
… or as you’ll need to do after the install, change the Boot List Option from Legacy to UEFI:
Wednesday, December 9, 2015
Disabling tabs displayed in Citrix StoreFront 3.x
I’ve recently been asked a few times by clients and colleagues about the ability to hide the new X1 StoreFront interface’s Favorites, Apps and Desktop tabs and as I don’t have a blog post demonstrating it, I thought I’d write this quick post so I could direct these questions to it.
Hiding the Favorites Tab
To hide the Favorites tab as shown in the screenshot below:
… simply launch the Citrix StoreFront console, navigate to Stores, select the store you would like to hide the tab and the click on the Disable User Subscriptions option on the right:
You will be briefly presented with the following prompt:
Click on Yes to complete the configuration.
Hiding the Apps or Desktops Tab
To hide the Apps or Desktops tab as shown in the screenshot below:
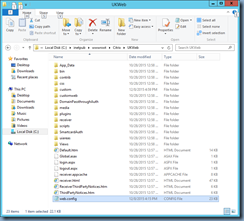
… simply navigate to the C:\inetpub\wwwroot\Citrix\<StoreName>Web directory, open the web.config file with Notepad:
Then search for either showAppsView or showDesktopsView which will bring you to the following section:
<userInterface autoLaunchDesktop="true" multiClickTimeout="3"
enableAppsFolderView="true">
<workspaceControl enabled="true" autoReconnectAtLogon="true"
logoffAction="disconnect" showReconnectButton="false" showDisconnectButton="false" />
<receiverConfiguration enabled="true" downloadURL="ServiceRecord/GetDocument/receiverconfig.cr" />
<uiViews showDesktopsView="true" showAppsView="true" defaultView="auto" />
<appShortcuts enabled="false" allowSessionReconnect="false" />
</userInterface>
Modify the true option for the respective tabs by changing them to false if you would like to hide them.
The following is an example of a StoreFront store with the Favorites and Apps tab hidden: