I ran into an issue today that got me frustrated not because I couldn’t solve right away but because I’ve come across this before but forgot what I did to solve it so now that I’ve resolved the issue, I figure I’d blog it so I can reference this blog in the future.
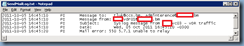
I encountered the problem when I completed the setup of a new Kiwi Syslog server which allowed me to send VMware Data Recovery reports and logs to and in turn email recipients so they would know whether the daily backups were successful or not. The environment had Exchange Server 2010 as their messaging service and I’ve configured numerous Exchange Receive Connectors for mail relaying for various devices but as I completed my syslog configuration and executed a test email to be sent to my email address, the email never came. I initially thought it was something minor such as firewall or IP address so I went ahead and checked the obvious. After going through the configuration numerous times to verify I haven’t made any mistakes, I realized that I wasn’t anywhere closer to solving the problem. Seeing how I wasn’t really getting anywhere, I began reviewing the logs from the syslog server which showed the following:
2011-10-05 16:45:10 PI Message to: tluk@ccs.bm, adminterence@domain.bm
2011-10-05 16:45:10 PI Message from: vdr01@domain.bm
2011-10-05 16:45:10 PI Subject: Syslog message from vc03 - vDR traffic
2011-10-05 16:45:10 PI Date: Wed, 05 Oct 2011 16:45:10 –0300
2011-10-05 16:45:20 PI Mail error: 550 5.7.1 Unable to relay
Then I proceeded to turn on verbose logging on the Exchange 2010 Hub Transport server’s receive connector handling the connection and navigated to the path:
C:\Program Files\Microsoft\Exchange Server\V14\TransportRoles\Logs\ProtocolLog\SmtpReceive
… where the log was written:
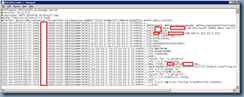
Opening up the logs showed the following:
#Software: Microsoft Exchange Server
#Version: 14.0.0.0
#Log-type: SMTP Receive Protocol Log
#Date: 2011-10-05T19:17:57.149Z
#Fields: date-time,connector-id,session-id,sequence-number,local-endpoint,remote-endpoint,event,data,context
2011-10-05T19:17:57.149Z,CAS01\VC03,08CE51AA847AC9C0,0,10.10.1.59:25,10.10.1.53:49654,+,,
2011-10-05T19:17:57.149Z,CAS01\VC03,08CE51AA847AC9C0,1,10.10.1.59:25,10.10.1.53:49654,*,SMTPSubmit SMTPAcceptAnySender SMTPAcceptAuthoritativeDomainSender AcceptRoutingHeaders,Set Session Permissions
2011-10-05T19:17:57.149Z,CAS01\VC03,08CE51AA847AC9C0,2,10.10.1.59:25,10.10.1.53:49654,>,"220 CAS01.domainnet.com Microsoft ESMTP MAIL Service ready at Wed, 5 Oct 2011 16:17:56 -0300",
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,3,10.10.1.59:25,10.10.1.53:49654,<,EHLO vc03,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,4,10.10.1.59:25,10.10.1.53:49654,>,250-CAS01.domainnet.com Hello [10.10.1.53],
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,5,10.10.1.59:25,10.10.1.53:49654,>,250-SIZE 10485760,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,6,10.10.1.59:25,10.10.1.53:49654,>,250-PIPELINING,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,7,10.10.1.59:25,10.10.1.53:49654,>,250-DSN,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,8,10.10.1.59:25,10.10.1.53:49654,>,250-ENHANCEDSTATUSCODES,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,9,10.10.1.59:25,10.10.1.53:49654,>,250-AUTH,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,10,10.10.1.59:25,10.10.1.53:49654,>,250-8BITMIME,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,11,10.10.1.59:25,10.10.1.53:49654,>,250-BINARYMIME,
2011-10-05T19:17:57.164Z,CAS01\VC03,08CE51AA847AC9C0,12,10.10.1.59:25,10.10.1.53:49654,>,250 CHUNKING,
2011-10-05T19:17:57.274Z,CAS01\VC03,08CE51AA847AC9C0,13,10.10.1.59:25,10.10.1.53:49654,<,RSET,
2011-10-05T19:17:57.274Z,CAS01\VC03,08CE51AA847AC9C0,14,10.10.1.59:25,10.10.1.53:49654,*,Tarpit for '0.00:00:05',
2011-10-05T19:18:02.290Z,CAS01\VC03,08CE51AA847AC9C0,15,10.10.1.59:25,10.10.1.53:49654,>,250 2.0.0 Resetting,
2011-10-05T19:18:02.290Z,CAS01\VC03,08CE51AA847AC9C0,16,10.10.1.59:25,10.10.1.53:49654,<,MAIL FROM: <vdr01@domain.bm>,
2011-10-05T19:18:02.290Z,CAS01\VC03,08CE51AA847AC9C0,17,10.10.1.59:25,10.10.1.53:49654,*,08CE51AA847AC9C0;2011-10-05T19:17:57.149Z;1,receiving message
2011-10-05T19:18:02.290Z,CAS01\VC03,08CE51AA847AC9C0,18,10.10.1.59:25,10.10.1.53:49654,>,250 2.1.0 Sender OK,
2011-10-05T19:18:02.305Z,CAS01\VC03,08CE51AA847AC9C0,19,10.10.1.59:25,10.10.1.53:49654,<,RCPT TO:<tluk@ccs.bm>,
2011-10-05T19:18:02.305Z,CAS01\VC03,08CE51AA847AC9C0,20,10.10.1.59:25,10.10.1.53:49654,*,Tarpit for '0.00:00:05',
2011-10-05T19:18:07.321Z,CAS01\VC03,08CE51AA847AC9C0,21,10.10.1.59:25,10.10.1.53:49654,>,550 5.7.1 Unable to relay,
2011-10-05T19:18:07.337Z,CAS01\VC03,08CE51AA847AC9C0,22,10.10.1.59:25,10.10.1.53:49654,<,QUIT,
2011-10-05T19:18:07.337Z,CAS01\VC03,08CE51AA847AC9C0,23,10.10.1.59:25,10.10.1.53:49654,>,221 2.0.0 Service closing transmission channel,
2011-10-05T19:18:07.337Z,CAS01\VC03,08CE51AA847AC9C0,24,10.10.1.59:25,10.10.1.53:49654,-,,Local
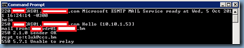
What I noticed to be consistent was the error:
550 5.7.1 Unable to relay
The hunch I immediately had was that Exchange was not allowing me to relay email out to a recipient at a domain that wasn’t internal so I went ahead to do a few telnet tests:
To an external email address
220 CAS01.domain.com Microsoft ESMTP MAIL Service ready at Wed, 5 Oct 2011 16:24:14 –0300
helo
250 CAS01.domain.com Hello [10.10.1.53]
mail from:vdr01@domain.bm
250 2.1.0 Sender OK
rcpt to:tluk@ccs.bm
550 5.7.1 Unable to relay
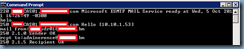
To an internal email address
220 CAS01.domain.com Microsoft ESMTP MAIL Service ready at Wed, 5 Oct 201
1 16:26:49 -0300
helo
250 CAS01.domain.com Hello [10.10.1.53]
mail from:vdr01@domain.bm
250 2.1.0 Sender OK
rcpt to:adminerence@domain.bm
250 2.1.5 Recipient OK
Solution
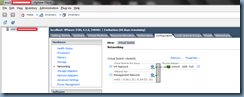
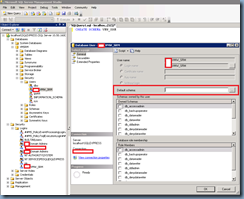
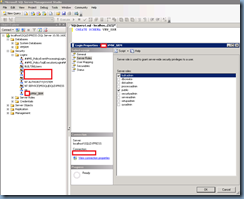
What the telnet tests revealed was that I had no issues relaying mail to domains that Exchange hosted internally which was no surprise because the receive connector I used was allowing other scanners and printers to relay email. This was when I remembered that Exchange handled mail relay requests for internal and external domains based on the settings configured in the Authentication tab for the Receive Connector. Opening the receive connector’s properties and navigating to the Authentication tab will show the following options:
- Transport Layer Security (TLS)
- Enable Domain Security (Mutual Auth TLS)
- Basic Authentication
- Offer Basic authentication only after starting TLS
- Exchange Server authentication
- Integrated Windows authentication
- Externally Secured (for example, with IPsec)
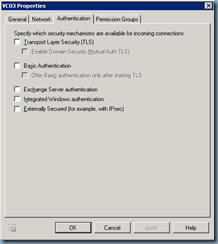
Without dragging this on, the security mechanism to enable so relaying servers can send to external recipients is the option:
Externally Secured (for example, with IPsec)
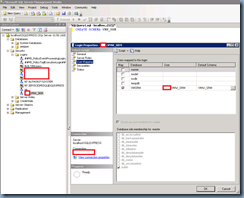
With this option selected, you will also notice that it will also be mandatory to select the option:
Exchange servers
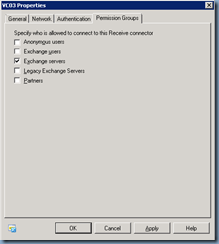
The configuration shown above
Authentication –> Externally Secured (for example, with IPsec)
Permissions Group –> Exchange servers
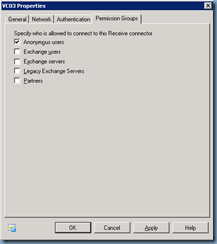
… will allow you to relay emails out to an external recipient with an internal email address. If you were to use an external domain as the sender address, you’ll also need to check the option:
Permissions Group –> Anonymous
Hope this helps anyone who might be experiencing the same problem as I did today and I’m glad I’ll be able to reference this post when I get that “déjà vu” feeling again in the future when I’m bound to come across this again.